Enterprise Email Infrastructure: Security Baseline and Best Practices - DKIM
DomainKeys Identified Mail (DKIM)
DKIM is an email authentication method designed to detect forged sender addresses in emails. It uses a pair of cryptographic keys – a private key to sign outgoing emails and a public key published in the DNS for verifying the signature.
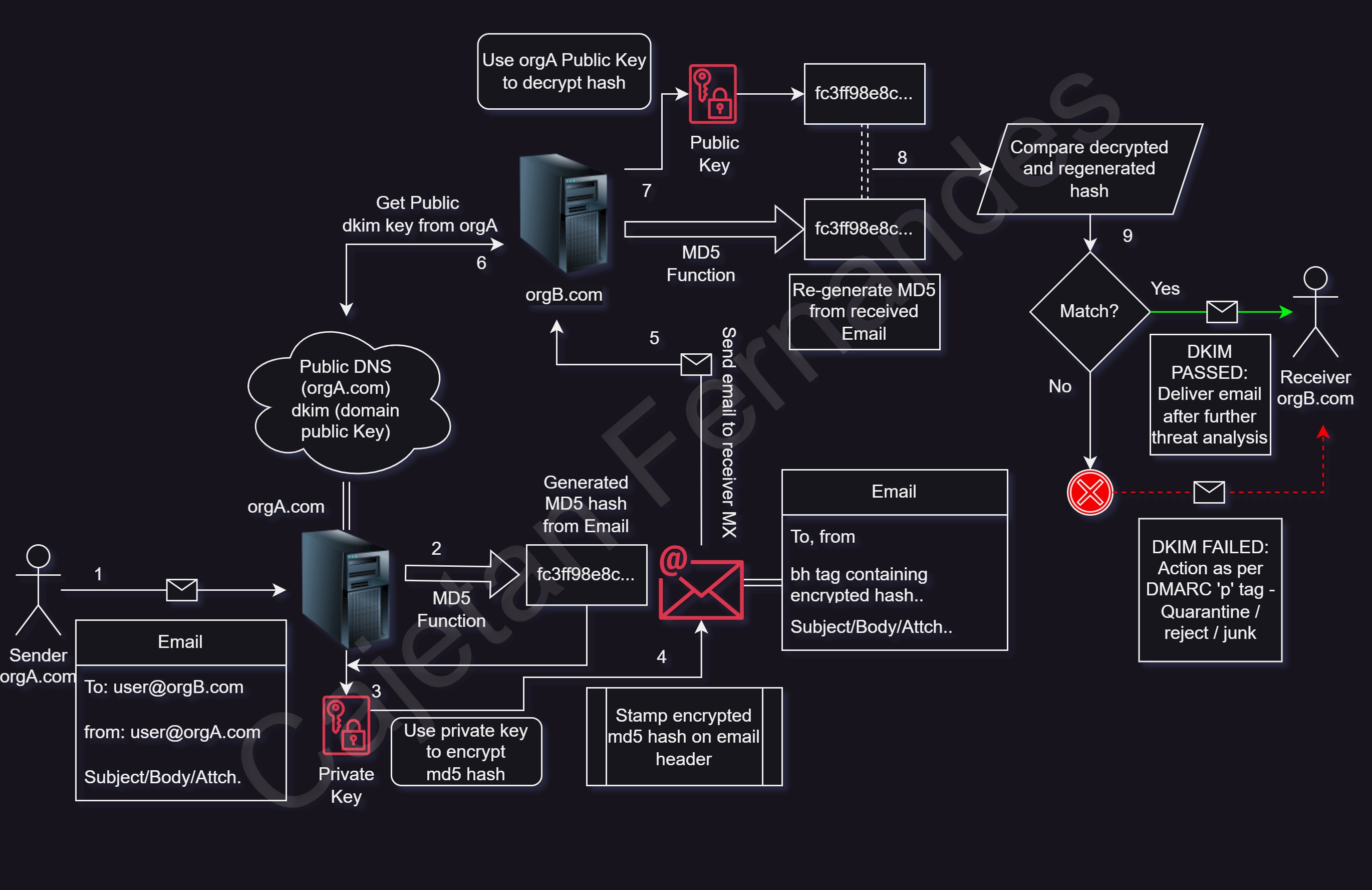
It is is an email authentication method designed to detect forged sender addresses in emails, a technique often used in phishing and email spam. By adding a digital signature to the headers of an email, DKIM allows the receiver to verify that an email claiming to come from a specific domain was indeed authorized by the owner of that domain. This helps to ensure the integrity and authenticity of the email.
How DKIM Works
- Key pair generation
- Email signing
- DNS record publication
- Email reception and verification
- Upon receiving an email, the recipient's server retrieves the public key from the sender's DNS records.
- The server then uses this public key to verify the digital signature in the DKIM-Signature field.
- If the signature is valid, it confirms that the email has not been altered and is indeed from the claimed domain.
The domain owner generates a public-private key pair. The private key is securely stored on the email server, while the public key is published in the DNS (Domain Name System) records.
When an email is sent from the domain, the server uses the private key to generate a digital signature for specific parts of the email (usually the header and the body). This signature is then added to the email headers as a DKIM-Signature field.
The public key is published in the DNS records of the domain. This is done using a TXT record type under a selector prefix (_domainkey). For example:
@ IN TXT selector1._domainkey.example.com("v=DKIM1; k=rsa; p=public-key-here")• Here, 'selector1' is a unique identifier that allows the domain owner to rotate keys by simply changing the selector.
DKIM-Signature header
The DKIM-Signature header contains several important fields:
- v=: DKIM version (typically DKIM1).
- a=: The algorithm used for signing (e.g., rsa-sha256).
- d=: The domain of the sender.
- s=: The selector used to locate the public key in DNS.
- bh=: The hash of the body part of the email.
- b=: The actual digital signature.
- h=: A list of signed headers.
Example of a DKIM-Signature header:
DKIM-Signature: v=1; a=rsa-sha256; d=example.com; s=selector1;
c=relaxed/simple; q=dns/txt; i=@example.com;
h=From:To:Subject:Date;
bh=ZXhhbXBsZWhhc2h2YWx1ZQ==;
b=abc123dkimsignature==Benefits of DKIM
- Improved Email Security:
- Enhanced Domain Reputation
- Compliance with Global Standards
- Integrity Verification
DKIM helps to reduce the likelihood of email spoofing, phishing, and impersonation by ensuring that emails are indeed from the claimed domain.
Consistent use of DKIM can improve a domain's reputation with email service providers, potentially leading to better email deliverability rates.
DKIM is part of a broader email authentication framework that includes SPF (Sender Policy Framework) and DMARC (Domain-based Message Authentication, Reporting & Conformance). Using DKIM helps organizations comply with these standards.
DKIM provides a means for verifying that the content of an email has not been tampered with during transit.
Implementation
Implementing DKIM (DomainKeys Identified Mail) for your domain involves several steps, including generating key pairs, updating DNS records, configuring your email server to sign outgoing emails, and verifying the setup.
If you use a cloud based Email service provider like Microsoft 365, you can follow their documentation on directly setting up DKIM as per their implementations; however, if you use your own internal mail server, here's an example of how you can implement DKIM:
- Generate DKIM Keys
- Choose a DKIM Selector: A selector is a string used to differentiate between multiple DKIM keys. Choose a unique selector name, such as default or selector1.
- Generate Key Pairs: Use a tool to generate a public-private key pair. Many email servers and third-party tools can help with this. Here’s an example using OpenSSL:
OPENSSL Generate RSA Key Pairs
openssl genrsa -out dkim-private.key 2048 openssl rsa -in dkim-private.key -pubout -out dkim-public.key• dkim-private.key is your private key (keep this secure).
• dkim-public.key is your public key (you’ll publish this in DNS).
- Publish the DKIM Public Keys in your Public DNS provider
- Format the Public Key: The public key needs to be in a specific format for DNS. It should be one continuous string without line breaks. Here’s an example format:
DKIM Public Key Format
v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDFG... - Create a DNS TXT Record: Add a TXT record to your DNS settings. The name of the record will be a combination of your selector and _domainkey (e.g., selector1._domainkey.example.com).
DNS TXT RECORD for DKIM
Name: selector1._domainkey Type: TXT Value: "v=DKIM1; k=rsa; p=MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDFG..." - Add the Record to Your DNS: Use your DNS provider’s interface to add the TXT record. It may take some time for the DNS changes to propagate.
- Format the Public Key: The public key needs to be in a specific format for DNS. It should be one continuous string without line breaks. Here’s an example format:
- Configure Your Email Server
Configure your email server to sign outgoing emails with your DKIM private key. The exact steps depend on the email server software you are using.
- Verify DKIM Configuration
- Send a Test Email: Send an email from your domain to an external email address.
- Check Email Headers: Examine the email headers of the received email to ensure the DKIM-Signature is present.
- Use Online Tools: Utilize online DKIM verification tools to check if your emails are correctly signed. Some popular tools include:
- Monitor and Maintain
Discussed in the next section: Best practices
Best Practices of DKIM
- Regular Key Rotation:
- Use Strong Cryptographic Algorithms:
- Monitor DKIM Implementation:
- Ensure DNS Availability:
Rotate DKIM keys periodically to minimize the risk of key compromise.
Prefer stronger algorithms like rsa-sha256 over weaker ones to ensure robust security.
Use DMARC reports to monitor the effectiveness of DKIM and identify any issues with email authentication.
Maintain a reliable DNS infrastructure to ensure the availability of public keys for verification.
Conclusion
Conclusion DKIM is a crucial component of modern email security, providing a mechanism to authenticate emails and protect against various types of email-based attacks. While its implementation can be complex, the benefits of improved email integrity, security, and domain reputation make it a valuable tool for any organization. By following best practices and integrating DKIM with other email authentication methods like SPF and DMARC, organizations can create a robust defense against email fraud and abuse.